E-Mail security
Though a fair amount of security breaches can be blamed on equipment (example: router firmware with vulnerabilities), the weakest link is the user in most cases. This could be a user that configured a firewall in the wrong way or a user that left the default administrator name and password to the server but the most common way a user is at least partially responsible for a breach is by falling victim to phishing or spear-phishing attacks. A lot of people are simply not educated on the subject and/or ignore the knowledge they do have. Phishing attacks used to be fairly easy to spot but lately they have gotten surprisingly good and efficient. A phishing attack can happen to anyone and no matter how good they are, there are always signs by which an attack like that can be spotted, you just have to know where to look.
1. Do you know the sender? (From: )
Is the sender someone that has communicated with you before? Check to see if it is a person or organization you know or if it is an unknown, weirdly formatted email address. If it is someone you know it does not mean the email is safe. That person’s computer could be infected with malware that is sending out phishing emails without the person knowing. If it is not someone you know pay extra attention to the rest of the email.
2. Are you the only recipient? (To: )
Does the “To: ” field list you? Or does it show a big list of unknown and weirdly formatted e-mail addresses and you are just one of them? If the latter is the case, proceed with caution because this is usually a sign of a spam or phishing e-mail.
3. Does the date make sense? (Date: )
If the e-mail came from someone you know, was it sent at a time that person is usually sending out e-mails? If you receive an e-mail from a trusted source that usually does all of the e-mailing during normal business hours but the date shows it was sent at 4AM, something might be off.
4. Does the subject make sense? (Subject: )
And this of course depends mostly on the contents of the email but also the sender. If the subject shows “Hi, it’s been a while!” but you have seen or spoken to that person just a few days ago and the contents of the email are money related, something does not add up. See if the subject is relevant and matches the contents of the e-mail.
5. Analyze the contents of the email.
Some signs the e-mail may be spam or a phishing attack are
– bad grammar and spelling errors
– an unusual amount of links you can click on
– unusual requests being made about your personal information
– pretty graphics and layout do not mean the sender is trustworthy
– (and this one is often underrated and ignored) an uncomfortable gut feeling when reading the e-mail.
If the e-mail contains links, hover your mouse over them before you click on them, this will cause a small pop-up to show the actual web address of that link. See if the web address matches the link in the e-mail and the context of the contents. A link inside of an e-mail from a bank that actually links to “http://x6usy634.advertisements.net”(example) is suspicious. Also, do not read to fast. If the web address does look good it may still be a spoofed website under control of the attackers. If the web address for that shoe sale link shows “http://bankofarnerica.com” you may be inclined to click on it. Look closely. While bankofamerica.com is a known and trusted website, bankofarnerica.com is not (the ‘m’ is actually an ‘r’ and ‘n’ making it look like an ‘m’. It may be a website set up by phishers to mimic the bank of america website all for the purpose of you entering your login information which they will then have and use or sell.
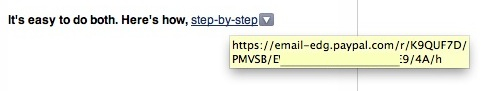
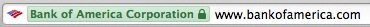
If you received an e-mail from bank of america asking you to “click here for more information” or “click the link below to see the message”, don’t click on it. Instead open a browser window and type in the bank of america website yourself. If there is indeed an important message waiting for you, the actual bank of america website will show you. This way you can also see if the browser address bar shows you the lock icon that proves you are at the actual bank of america website. Of course I am using the bank of america as an example but this goes for any company/corporation.
6. Do the attachments look ok?
Do the attachments have normal filenames and extensions? Should an email like this even have attachments, are they needed? The attachment shows it is a .doc Word Document but the size is unusual. Be suspicious of attachments and always have an antivirus application scan them before opening. If a script or application is hidden inside of the attachment you may be lucky enough that OS X’s gateKeeper catches it and warns you but in case it doesn’t you could be infecting your Mac with malware.
You can even go as far as checking the headers of each e-mail and i do recommend this for e-mails that you do not trust. If a header shows that the ‘info@bankofamerica.com’ e-mail was sent through ‘0000013e388fc993-4832d1d9-dff5-4e@amazondres.com’ or ‘765765asdf@hotmail.com’ you can be fairly sure the e-mail did not come from bank of america. Large corporations like that have their own e-mail servers and do not rely on 3rd party e-mail hosts to handle their communications. To view the full headers of an email message, click on the suspicious e-mail and in Mail’s menu click ‘View > Message > All Headers’
So you may have heard the term ‘phishing’ but what is is? And what is this ‘spear-phishing’ i mentioned earlier?
Phishing: “Phishing is the act of attempting to acquire information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication.” excerpt from Wikipedia, more info here.
Spear-Phishing is the same as Phishing. The difference is that the attack is targeted towards a specific person or group. So these types of phishing e-mails can call you by name and have more information in it specific to you (like information that can be obtained from your social media pages if you have not secured them properly or a phone call that was overheard by someone).
As you can see there is a lot going on in a typical e-mail that can be used to trick (or social engineer) you into giving up sensitive information. Always keep an eye out for phishing attacks and do not let your guard down. You have probably already received numerous phishing e-mails and you did not see them because they were caught by your spam filter. If you’re online, you are a target that eventually phishers will go after.
Great tips here, thank you!
It’s hard to come by educated people about
this subject, however, you seem like you know what you’re talking about!
Thanks