Why antivirus is needed, even on Macs
The other day i was doing some routine maintenance on my brother’s iMac. Updates, permissions repair, etc. when i opened safari to download the latest Flash player update (i always get it straight from the source) i noticed a weird banner in the bottom of the display and after a few seconds a second banner showed up on the right. I know what the Adobe website is supposed to look like and this was not it. I opened the Safari preferences and checked his installed extensions and saw Yontoo was installed. Weird, i know Apple updated it’s XProtect some time ago to block Yontoo, how could it still be here? (XProtect, or File Quarantine, is OS X’s built-in malware protection) Yontoo does not exploit any vulnerabilities in OS X but it does generate a lot of ads on websites you visit and is therefore considered ‘AdWare’ by some but ‘Malware’ by others. Though i did not understand how OS X allowed it to be there, i was not too concerned as there are multiple versions and not all are detected. I also noticed two other extensions called Codec-M and Torrenthandler. Torrenthandler is one of the ways the ‘bad’ version of Yontoo is delivered. Codec-M is an aggressive AdWare plugin and collects information about your browsing habits, therefore considered ‘SpyWare’.
Checking his downloads folder i noticed he had downloaded ‘DropDownDealsSetup.dmg’ from dropdowndeals.com (visit at your own risk). The included Drop Down Deals Installer is known to install Yontoo on target systems. A scan of the installer later on with Norton shows it is indeed the delivery method for Yontoo, even the uninstaller installs it!
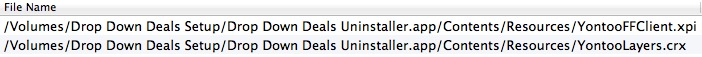
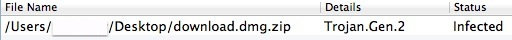
I was able to trace the Codec-M back to a ‘Download.dmg.zip’ and while OS X had no problem with me opening the .zip and running the installer (XProtect did not warn me), a scan with Norton later on did show the file was infected and Norton immediately quarantined the .dmg before i could open it.
I was unable to find the source of Torrenthandler.
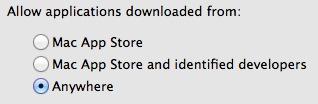
Wondering how this nice collection of Ad/Spy/Malware got on his system i looked at the Gatekeeper settings (System Preferences > Security & Privacy > General) and found it was set to allow applications to be opened from anywhere. Certainly not how i left it since last time i did maintenance. This is probably how my brother was able to install the ‘ware’ on his system without much resistance from OS X but why did XProtect not do it’s job?
To verify if XProtect was up to date i ran a terminal command “defaults read /System/Library/CoreServices/CoreTypes.bundle/Contents/Resources/XProtect.meta LastModification” and it showed me XProtect was last modified the day before. I even ran another command that forces an update “sudo /usr/libexec/XProtectUpdater” and it said no new version was available. Weird. When i transferred the infected files to my own Mac and opened them in a virtual machine i have set up just for test purposes like this, XProtect flagged the file and did not allow me to open it. Instead it informed me the malware was found and gave me the option to eject the disc image.
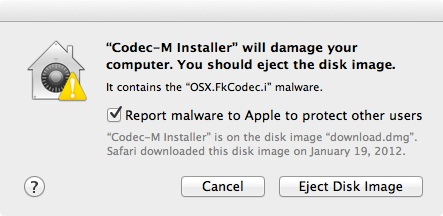
As you can see from the screenshot above, the infected file was downloaded on January 19th, 2012, i verified this on my brother’s computer by looking at the file creation date. This is interesting because the OSX/FkCodec-A (Codec-M) malware was not identified until April 20th, 2012. Either my brother had somehow stumbled upon this malware long before it was discovered by antivirus companies or the file creation date was off.
Either way, XProtect was up to date and it still allowed me to run the COdec-M installer, was XProtect broken somehow?
After some searching i was unable to find out if XProtect is able to detect malware that has already been installed. As Apple has used XProtect to block older versions of Flash and Java that are already installed on a system, it should be able to detect already present malware as well.
Anyhow, i no longer trusted XProtect’s ability to keep my brother’s Mac safe so i installed Norton Antivirus and scanned his entire drive.
It found the DropDownDealsSetup.dmg, Download.dmg.zip and all traces of Yontoo, Torrenthandler and Codec-M and deleted it. It even found a few Windows viruses in old email attachments. This goes to show that while OS X is pretty well protected, the protection can malfunction. Also, Apple usually takes it’s time in updating XProtect giving Mac users a greater chance to download, open and install potential malware.
I fixed XProtect by re-installing the latest 10.8.3 Combo Update. I tested it by trying to run the Codec-M installer which was blocked right away.
Lessons learned:
– These days having an antivirus application installed on your Mac is a good idea. Us Mac users have been able to hide behind “Macs can’t get infected” long enough, it simply does not hold true anymore. For a good test and comparison on available antivirus for Mac have a look here. Leave the protection against malware to the professionals that have teams working on nothing but this 24/7, Apple has proven to simply be too slow in updating it’s protection.
– Built-in defenses can be disabled and/or can malfunction. Leave Gatekeeper set at “Mac App Store and identified developers”, if you really want to open a file that does not meet these criteria just right-click on it and select ‘open’ from the menu. This will still present you with a Gatekeeper warning only this time it gives you the option to open the file as well.
– Be smart when downloading files off the internet, use common sense.
– Stay up to date about the latest threats on websites such as this.
> After some searching i was unable to find out if XProtect is able to detect malware that has already been installed. As Apple has used XProtect to block older versions of Flash and Java that are already installed on a system, it should be able to detect already present malware as well.
XProtect relies on the older “Quarantine” system which is used by selected applications to tag files when they are first downloaded to the hard drive. There is some capability for subsequently produced files to inherit this tag (e.g. unzipped files and executables which are Finder copied to /Applications/), but many other parts are not so tagged. No quarantine check, no XProtect check. For this reason, signatures of components are rarely provided.
But Apple also uses the MRT (which probably stands for Malware Removal Tool) to detect and remove “commonly found malware” which does appear to remove most of those components. The MRT is now provided with every OS X Security and Java update. It only runs once and notifies the user only if it finds something. There is no documentation on what it considers to be “common.”
Obviously this isn’t nearly the protection provided by 3rd party A-V software, but I think it’s a bit better than your impressions indicate.
Thanks for the feedback Al, If the MRT is included in every update now (i thought it was a one time thing for Flashback) then a good test of this will be to update my virtual machine used for testing to the latest 10.8.4. Haven’t done this yet as i want all testing to be done under identical conditions. I’ll clone the VM then update that infected OS to 10.8.4 which has the latest security update in it. I’m curious about the result and i’ll post back once this is done with my findings.
I have updated the infected 10.8.3 machine to 10.8.4 and after the restart i found various versions of MacKeeper, Imunizator, KitM still launching on login. I found no warnings from an MRT, nothing removed and nothing disabled. With these results i do not believe any kind of MRT is included in security updates (i have done no research on this though) and if it is included it is not worth the time they spend on building it as every variant of old malware should be detected by now. If a user is infected by a piece of malware before Apple updates their XProtect to protect against that specific malware, OS X will never know it’s there unless a specific removal tool is released for it.