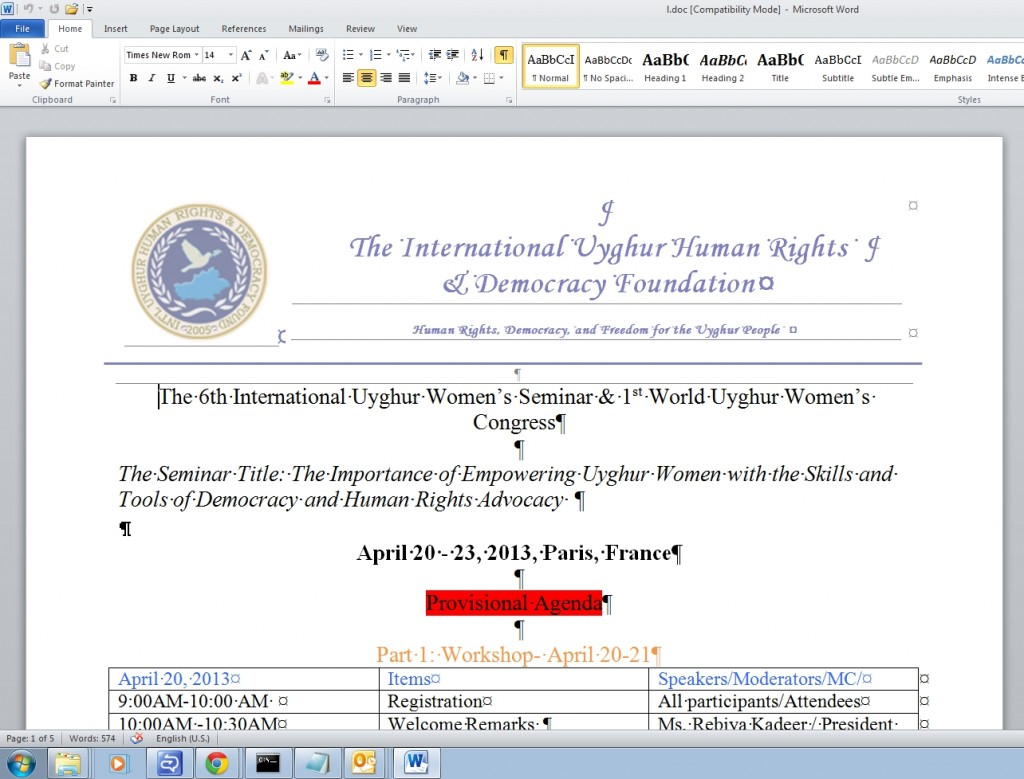
Word document containing Mac malware found
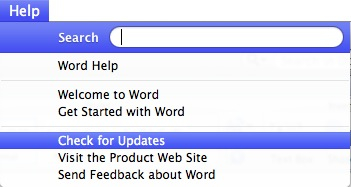
Today F-Secure has made note of a Word document that is designed to infect Macs with malware. The Word document claims to be about the “6th International Uyghur Women’s Seminar & 1st World Uyghur Women’s Congress”, run by the International Uyghur Human Rights & Democracy Foundation. The document installs the malware by exploiting a vulnerability in Word, a vulnerability that has been fixed in 2009 by Microsoft. It drops a backdoor for PowerPC and Intel Macs that masquerades as a Real Player Updater.As the document targets the Uyghur people it is unlikely that anyone is not Uyghur or associated with Uyghur will ever see or be interested in this document. Also the version of MS Office needs to be outdated for the exploit to work. To make sure you are not at risk of being infected by this document, update your Office to the latest version by clicking on the ‘Help’ menu from within any of the Office applications, then select ‘Check for Updates’ and install whatever updates are available. Keep checking until there are no more updates available.
This malware turns out to be an altered version of CallMe. Mostly the same just with different file names and the server it calls home to once installed. As said, your chances of encountering this malware are slim but it goes to show how important it is to keep your software up to date. Just because a certain version of malware is old doesn’t mean it can’t pose a threat anymore. As far as i know all major antivirus developers have updated their databases so this document can be identified and deleted as soon as it enters your system.
The malware uses “alma.apple.cloudns.org” as the command and control server, make sure this is blocked if it shows up in applications such as Little Snitch. Posing as a RealPlayer Update it installs itself in these directories on a Mac:
~/Library/Application Support/.realPlayerUpdate
~/library/launchagents/realPlayerUpdate.plist
or
/Library/Application Support/.realPlayerUpdate
/library/LaunchDaemons/realPlayerUpdate.plist
If any outgoing connections are shows from the .realPlayerUpdate by Little Snitch, make sure they are blocked. Some hosts it contacts are:
alma.apple.cloudns.org
apple12.crabdance.com
update.googmail.org