Computer theft, how to prepare
If and when it happens, it usually happens to folks who were not prepared. So while we hope your computer will never get stolen it’s a good idea to prepare just in case. Preparations are quite simple, do not take up a lot of time and can save you a whole lot of grief if someday you do find your computer missing. Let’s begin.
Backup your data
A computer can be replaced, your data cannot. So make sure you have a good backup and keep that backup in a safe place. A Time Machine backup to an external hard drive is cute but if the computer gets stolen, the external drive will most likely be taken as well. For some tips on backing up check out these articles here and here.
Encryption
Strangers accessing your data is the main concern when your computer gets stolen. Making sure your sensitive data is properly encrypted should give you enough time to act. Even if the encryption can be broken, a properly encrypted drive or folder takes a lot of time to brute force, this will give you enough time to change all your passwords, call your credit card company etc. OS X’s built-in FileVault is a good way to encrypt your home folder or your entire hard drive. If you feel this impacts the performance of your computer (test it before you assume it will) then use Disk Utility to create encrypted disk images you can use to store sensitive data in. To do this, open Disk Utility and click on ‘New Image’. A new window will pop up as shown below.
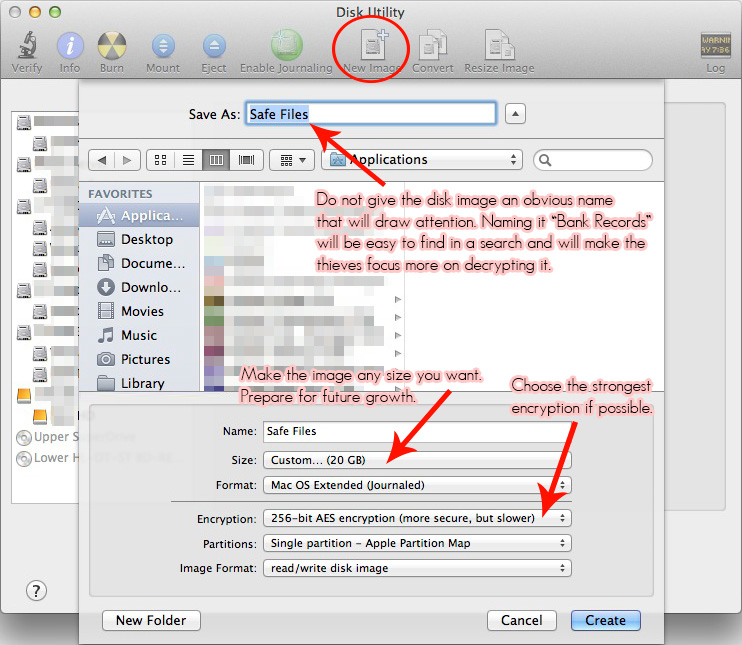
Once you have set everything up, click the Create button. Create a password and wait for the image to be created.
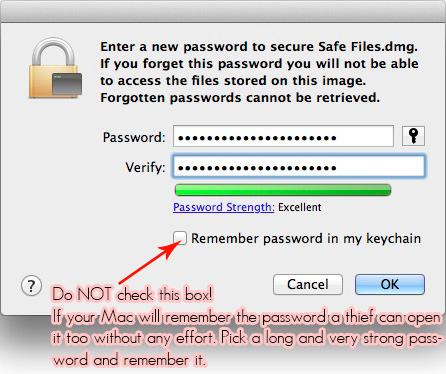
Set strong passwords
Encryption and protection is only as strong as it’s key, your password. I recommend setting multiple passwords.
Firmware password – This is a password that is set in the hardware of your Mac, it prevents someone to boot your Mac from another hard drive, flash drive, DVD or even the recovery partition. White the firmware password can be disabled if you know what you’re doing, it will still slow down a thief attempting to get to your data.
Login password – Make sure a password is required as soon as the computer starts up. Automatic login is fast and convenient but remember that anything convenient for you is convenient for thieves as well.
Screensaver password – This will require you to type your login password to get back to your desktop. If you are using your computer in an environment with multiple people, set your screensaver to start after a few minutes or start it manually when you walk away from your computer. This way you won’t have to worry about others snooping around in your data while you are away.
Keep in mind that passwords are no good if a thief extracts your hard drive and connects it to another computer. This is why encryption is so important. Thieves are not stupid, they are well aware that information is worth money and they will try to sell it. For more on passwords check out articles here and here.
Lock it down
Most Macs have built-in security slots that allow you to connect a cable or lock to it. While most of the solutions out there are no match for a pair of bolt cutters it will likely slow a thief down, maybe and hopefully to the point of giving up on the computer and focussing on your flatscreen TV. Here is what the security slot looks like on some different Macs.
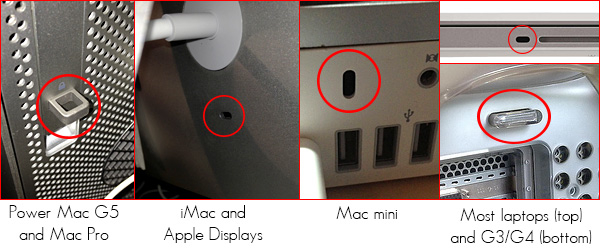
MacBook Airs and Retina MacBook Pros do not have the security slot. but there are solutions out there for these models as well. Desktop computers can be more easily and permanently locked in place using other parts of the computer frame like the hole in the iMac stand or one of the Mac Pro handles. Here are some suppliers of security products that can help you lock down your Mac.
Kensington
Apple Locks
Tryten
Register your equipment
Good luck finding the receipt when you really need it. You’ll need a serial number and/or other hardware information for the police report. This is where AppleSerialNumberInfo’s (ASNI) hardware registration page comes in. Simple and to the point it lets you create a free account and register all your hardware. Your serial numbers will be there in case you ever need them. Enter the serial number, place of purchase and date of purchase and you have one less thing to worry about. The website also has a very popular theft report system which allows you to register your Mac (or iDevice) as stolen. With the amount of traffic ASNI receives it is getting harder to sell stolen equipment once it has been registered on their page. Many vendors check serial numbers of products against ASNI’s database to see if it has been reported stolen and to see if the specs of the machine are what they should be. So, with all your serial numbers registered on the page and a button available to report that particular device stolen, it’s a breeze. You can register your equipment by visiting their website and clicking the ‘Login or Register’ button in the menu.
Once it’s gone the fight is not over
There are products that allow you to track and hopefully retrieve your stolen computer. Some of these also allow you to erase your data the next time the computer powers on and connects to the internet. While Apple does not allow firmware access to anyone these products are limited in their abilities so they have to be powered on, logged in and connected to the internet for them to work properly. Apple’s own Find My Mac feature (part of iCloud) does a good job in locating your Mac as soon as it pops up online and gives you the option to lock it down with a password or remotely wipe it. Products like Orbicule’s Undercover, Prey, Bak2U’s Phoenix and Absolute Software’s LoJack are a few of the available options that can help you track your stolen computer. I have used Undercover before and it performs really nice. The other products i have no personal experience with but i hear great stories about them.
There is nothing preventing you from using some or all of the above mentioned security measures simultaneously, in fact the more the better.
Then of course there is the cost that comes with having to buy new hardware and (depending on the value of the lost data) rebuilding the data. Insurance is always a good idea, this should at least take care of the hardware replacement costs. Being prepared is a good idea wether you will ever need them or not. These solutions have little to no impact on system performance (with the possible exception of encryption) and take little time to implement. Better safe than sorry!
2 thoughts on “Computer theft, how to prepare”