New Mac malware found – Janicab
Today researchers at F-Secure found a new piece of malware capable of infecting Macs. The malware is currently detected as:
Backdoor:Python/Janicab.A by F-Secure,
BackDoor.Janicab.1 by Dr.Web,
Python/Janicab.A by ESET,
Mal/BredZpRTL-A by Sophos,
TROJ_GEN.F47V0712 by TrendMicro.
While it is currently unknown if this is a Proof of Concept (PoC) or if it has been seen in the wild, F-Secure does suspect earlier versions of Janicab may be around as the Command & Control (C&C) servers show traffic history dating back to March 2013.
Janicab uses a trick placing a right-to-left override (RLO) character in the filename. This indicates to OS X that the filename should be read backwards as is done with some languages like Arabic or Hebrew. Because the fake extension is written backwards, once converted to right-to-left it’s the fake extension that reads real and the real extension that reads like a fake (.app then reads like .ppa). So the filename becomes RecentNews.ppa.pdf.
Once doubleclicked the code that is executed is an actual application causing the Finder to ask if you are sure you want to open this. As many users usually do not read these prompts and just click “Open” the fact that the text in the prompt may read backwards may be easily overlooked. The malware is signed by a valid Developer ID (just like KitM/Hackback) in this case belonging to Gladys Brady so regardless of your security settings the file will be able to open. Once the ‘Open’ button is clicked you will not be bothered again.
Once the .zip file is opened, with the Finder preferences set to default the file will look like this:

And when double-clicked the prompt will look like this: (backwards text)
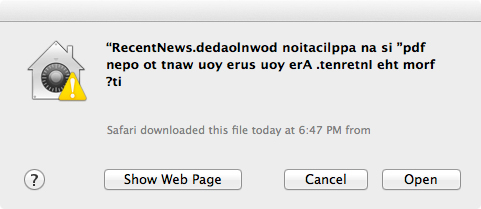
However when you set the Finder preferences to ‘Show all filename extensions’:
The file will look like this: (true extension)

And when double-clicked the prompt will look like this: (normal text)
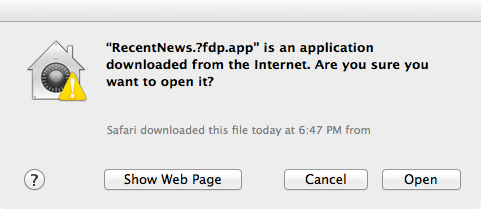
So simply looking out for prompts that have the text read backwards is not enough. If your Finder preferences are already set to show all filename extensions the prompt will read normal english. Also, depending on which application is used to open the .zip file, the file name can get a little messed up like this:

Once the RecentNews file is opened, a ‘file.pdf’ is opened in Adobe Acrobat or Preview displaying random russian stuff and the malware (or, Python operating under the malware’s instructions) starts contacting servers (in order):
hjdullink.nl at 85.17.242.81/www15.totaalholding.nl located in The Netherlands,
youtube.com at 208.117.244.54/cache.google.com located in US California,
111.90.152.210 located in Malaysia,
youtube-ui.l.google.com at 74.125.229.230/mia05s07-in-f6.1e100.net located in US California.
According to F-Secure these connections go to:
http://www.youtube.com/watch?v=DZZ3tTTBiTs (removed)
http://www.youtube.com/watch?v=ky4M9kxUM7Y (removed)
http://hjdullink.nl/images/re.php (not found)
The 111.90… IP appears to have something to do with a Google+ and Youtube account belonging to “sauidhiahdo uiahduia”. The account has only one video on it named ‘last vacation’ but this video has also been removed. The IP address has no history with VirusTotal other than the upload of an Apache HTML test page.
According to F-Secure, the Youtube servers are the malware’s C&C servers though I have found the other servers are being contacted far more often. Once the connection to the C&C servers has been made the malware will record audio and take screenshots and upload them to these servers. Though i have found no data has actually been uploaded since I installed the malware, the servers are pinged at a regular interval.
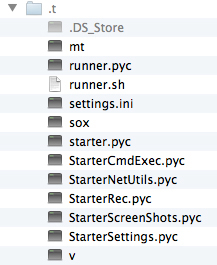
I have found no directory that stores these screenshots and audio recordings in preparation for upload. The only directory that is created is one named .t in the current user’s home directory. It’s invisible and contains a few Python executables.
If you have F-Secure, Sophos, Dr.Web, TrendMicro or ESET AV products installed you should be safe from this malware. If you do not use AV protection then you can manually remove the malware with the following instructions i found on thesafemac.com:
Removal should be fairly easy. However, you need to take great care. Be sure you have up-to-date backups of all your data, then read the instructions below carefully and follow them precisely!
The following command should be copied and pasted into the Terminal (which is found in the Utilities folder in the Applications folder). Do not try to re-type this command!A simple typo as simple as a space added in the wrong place could have disastrous consequences. Also, note that this will remove all cron jobs. That is the default state in Mountain Lion (Mac OS X 10.8), but much earlier versions of Mac OS X may differ (though I don’t know yet what versions of Mac OS X this malware is capable of infecting), and of course if you have created your own cron jobs, this will disrupt them.
crontab -r;rm -rf ~/.tOnce you have run this command, log out to ensure that all the malicious processes still loaded into memory are terminated. When you log back in, the malware should be gone.
As a general rule, read alerts and prompts before clicking any buttons. If you did not download a file or ask for it, treat it with caution. Keep an eye out for weird or double file extensions. Antivirus and Little Snitch are recommended. To easily spot fake file extensions, enable the Finder’s ‘Show all filename extensions’ in the Finder menu > Preferences > Advanced tab.
The F-Secure report can be found here.
UPDATE: Apple has revoked the Developer ID so opening this application now should result in the Finder giving you two options: Cancel or Move to Trash.
Comments and feedback welcome.
Great heads up! What are the chances of this malware hitting the masses like Flashback did? I don’t see much about this malware yet.
Thanks Nico. I don’t know where this malware originated or was first seen but so far the only time it has been seen in the wild is in the case where F-Secure spotted it. I doubt it will be as wide spread as Flashback as this malware is most likely included in phishing attacks or drive-by downloads from malicious sites, users are not tricked on a large scale like they were with Flashback. That said it is not this particular piece of malware but the new trick used (RLO) that is a cause for concern. Now that the trick is known there may be more malware coming trying to use it. As long as OS X falls for tricks like this it is probably a good idea to keep the “Show all filename extensions” preference enabled so it is easier to spot. With OS X 10.9 right around the corner this is something that may be addressed before the final release is out.