Detection VS Prevention, does your firewall have your back?
The internet is a dangerous place. Dangers no longer lurk in virtual dark alleys but can come from bright-lit main streets as well, you just won’t know where a threat will present itself. Apart from running antivirus, keeping your system, apps and plugins up to date and keeping Java disabled you often hear the mention of a firewall. “Enable your firewall!” is almost always included in the list of tips to keep your computer safe. But what does the firewall do? Does simply enabling it protect you from all the threats out there? Is every firewall the same? Do you even need a firewall at all?
I have always believed that if a good security feature is offered, it’s best to use it. OS X’s built-in firewall for example which I’ve mentioned before here, here and here. But recently I started looking into the concept of a firewall a bit deeper and realized there is more to a firewall than just blocking unwanted traffic. Protection is only half of the story, detection is equally important. I’ll share some basics and what I have learned so far.
What is a firewall
“A firewall is a software or hardware-based network security system that controls the incoming and outgoing network traffic by analyzing the data packets and determining whether they should be allowed through or not, based on a rule set. A firewall establishes a barrier between a trusted, secure internal network and another network (e.g., the Internet) that is not assumed to be secure and trusted.” according to Wikipedia and that about sums it up.
Why do I need a firewall
You want to be able to not have to worry about a stranger walking into your home, that’s why you have a front door with a lock on it. Those that are allowed in have been given a key to the door by you. A firewall basically does the same for your network, anyone without a key is not allowed in and those with a key (data you requested like a website, IM, email etc.) are allowed to enter. And just like burglars trying to force the lock on your door, there are online burglars (crackers) that are trying to find ways around, or through, the lock on your network. Another use for a firewall is restricting outgoing traffic like blocking facebook.com from the company network.
Different types of firewalls
Software – This would be the firewall that’s built into OS X and most other operating systems. 3rd parties like Objective Development, Norton and Intego also offer software firewall products. OS X’s built-in firewall is basic but offers some protection from things like port scans, pings and most unauthorized connection attempts. Pings are done to see if a host (your modem/computer) is online and responding. Port scans are done to see if there are holes or weak spots in your defenses that can be focussed on and exploited. For example I used Nmap to do a scan on the first 7000 ports of my Mac Pro. First with the built-in firewall disabled like it is by default and directly connected to my modem.
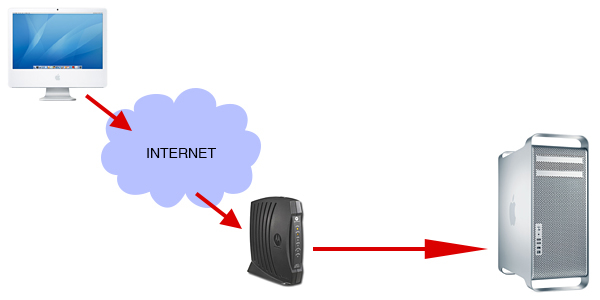
Here are the results:
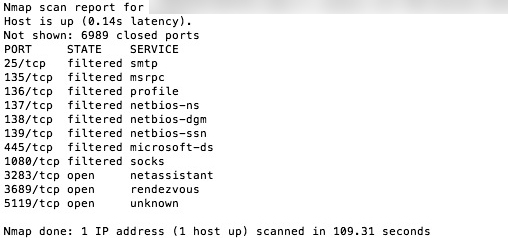
As you can see, a quick scan shows the host (Mac Pro) responding and telling me “Hi there! Here are the ports that are currently open and being filtered”. Not good. Keep in mind this is a very rare scenario these days. Now the average house has a few computers and/or devices that are connected to the internet so a router that offers at least some form of protection is always present. I did this test to show you that a firewall is needed. I enabled the firewall, configured it and ran the port scan again with the following result:
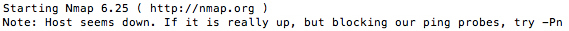
The firewall cloaked the existence of the Mac Pro on the network by using port stealthing, basically not responding to any ping or probe. As Nmap received no response it informed me the host seems down. But it also offered me a tip to deal with stealth mode so I tried again with the new command and got the following result:
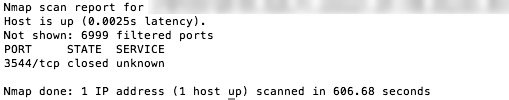
As you can see the OS X firewall does a pretty good job of hiding me from the internet. This time only one port was found and it is closed, meaning not accepting traffic. The OS X firewall also keeps log files which can be found in the Console.app (Applications > Utilities folder. Left column under /var/log look for appfirewall.log). An inspection of this log shows that a lot of connection attempts were made. Here is a small snippet of my firewall log on the Mac Pro after I performed the scan:
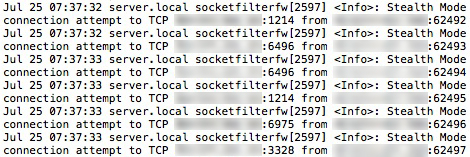
This shows me the date, time, origin and what was going on but if you don’t know what to look for in a log this may not mean much. Detection is equally (if not more) important as prevention so if you inspect your logs frequently an attack like this can be caught and you can take steps to defend yourself. Without proper logs or noone inspecting the logs these attacks can go on for a very long time until the Cracker finds a weak spot and possibly a way in. I have found that Norton’s firewall, included in the Internet Security suite, blocks these types of activity very well and also shows alerts to make sure they do not go unnoticed.
Apart from the very limited logging another issue with OS X’s firewall is that it only monitors incoming traffic. This is only half the job a firewall should be doing. For example if you are infected with malware (spyware, keylogger etc.) that is designed to stay hidden you may not notice it’s there until it is too late and valuable information was stolen. The malware will make an outgoing connection to a command&control server, receive instructions to take screenshots, record audio and/or capture your keystrokes and upload them to a remote host. The firewall does not monitor outgoing traffic so is unaware of this theft in progress. This is why I highly recommend Little Snitch as an added layer of security on your Mac.
An issue with software firewalls in general is the fact they are software firewalls. Software can be corrupted, bypassed or disabled by a person or cleverly crafted piece of malware. Something that is typically much harder to accomplish in a hardware firewall.
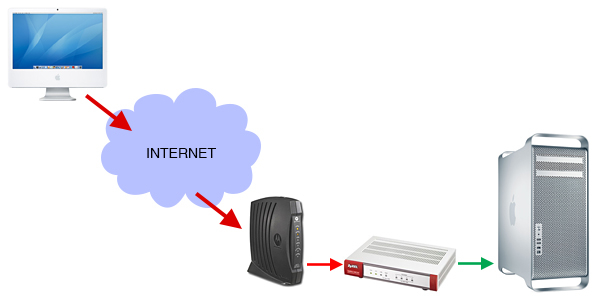
Hardware – This is most likely the router in your network and found in almost every home and office these days. Most modems now have a router built-in as well. The firewalls in most consumer grade modems/routers are called NAT firewalls and they are really not firewalls at all. The fact that they block unwanted traffic is a side effect of the way it functions. Here’s a very simple picture of this system:
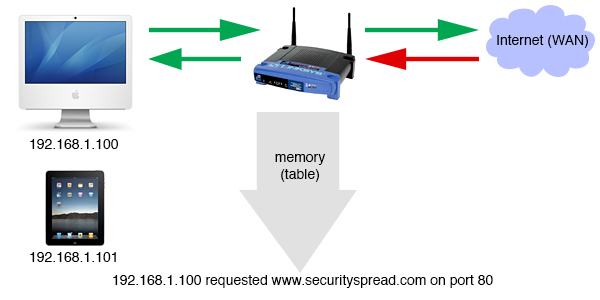
NAT (Detection usually poor, Prevention decent) – A router uses NAT (Network Address Translation) to convert one IP address into many. For example the IP address provided by your internet provider (ISP) is 74.263.263.23, your router hands out it’s own IP addresses to every device on the local network (LAN) like 192.168.1.100, 192.168.1.101 etc. but uses the ISP’s provided IP to communicate with the internet. It keeps a memory (or table) of the IP addresses it hands out and routes traffic accordingly. In the graphic above you can see that the iMac requested a website on a specific port, the router does the math “192.168.1.100 requested www.securityspread.com on port 80”, saves this in it’s table and sends the request out into the internet as “74.263.263.23 requested www.securityspread.com on port 80”. The web server responds and sends the requested website back to 74.263.263.23. The router knows that 192.168.1.100 asked for this site so it routes it to the right device. NAT keeps your network devices hidden from the internet, noone knows about the 192.x.x.x devices, just the IP assigned by your provider. Now the router receives the following “incoming connection from 300.40.50.88 on port 80”. It checks the table, sees that no local device requested this so the incoming connection is rejected. This is where the way NAT works also functions as a firewall, unrequested traffic is kept out.
Though not designed to be a firewall, it does a good job of acting as a basic form of one. A problem with using NAT as your firewall is that it is kind of stupid. It knows how to act as a router but not how to act as a firewall. You can ping, port scan and probe all day long and the NAT system will (hopefully) just reject the traffic because it is not in the table but it has no idea what’s going on. An unwanted request from a website is handled the same as an attack; no warnings, no heightened state of alert and no logs. In short, you may be under attack and even if you inspect your router logs you won’t know it’s happening. NAT also does not monitor any outgoing traffic, anything outgoing is considered OK (including the earlier mentioned malware stealing your information) and as it lacks intelligence like other firewall types it can be fooled by means of IP spoofing (data packets bearing a false IP address tricking the NAT into identifying it as coming from a trusted/requested source).
I performed the same port scan as before only this time I put an AirPort Extreme between my modem and Mac Pro. OS X’s firewall off and just letting the NAT firewall take care of keeping my network safe.
Here is the first result:
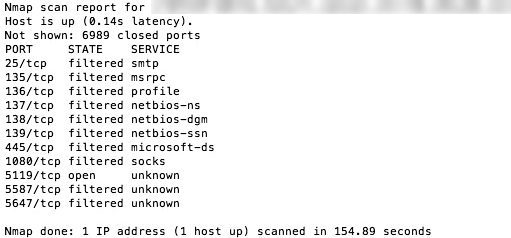
Quite a bit of info. Though not hidden, the good news is that most of the ports reported they were not accepting traffic. A decent job. Now I enabled the OS X firewall as an extra layer of security and ran the scan again:
Hmm, the OS X firewall only managed to hide two additional ports. All the filtered ports still show and that one open port too. This open port in my case belongs to iStat Server which I use to keep an eye on the Mac when I’m away from home. With iStat Server on and waiting for connections, the port scan was allowed through even though it was not a valid iStat request like it would get from my iPhone.
Ports that show as filtered, stealth or closed are considered safe. Noone can connect to them (apart from perhaps a skilled Cracker that may have tools and techniques to get around this). There is some debate about Filtered/Stealth VS Closed and which is better. Some say stealth is better because it hides you completely. A scanner/attacker does not know if an IP address simply has nothing connected to it or if the equipment on the other end is being hidden by means of stealth. This should cause an attacker to move on and scan for easier targets. If a scanner receives a ‘port closed’ response then he or she knows something is there and may be back later to see if any ports on that IP opened up. Others say closed is better because the scanner receives a ‘port closed’ response immediately. This is better because the scanner does not need as long to scan the whole network therefore not wasting valuable bandwidth. (it takes a lot longer for a scanner to figure out a port doesn’t exist or is stealthed than it does to see it’s closed). I guess both sides of the debate have valid points but in the end it does the same: block unwanted traffic. Whether a port shows as closed or stays hidden is your preference and depends on the capabilities and configuration of your router/firewall.
Open ports is something you simply do not want. In this case the open port is there because I set up iStat Server but if there is a vulnerability in iStat Server that can be exploited a port scan like this could be disastrous. Someone with malicious intent can connect to that port, use the exploit and gain access to my system/data. In my case it’s iStat, in your case it maybe another protocol or service.
But you check your firewall logs so even though your network is not as hidden (or closed off) as you’d like, if someone is trying to get in the logs will tell you. Afraid not. The AirPort Extreme (and the majority of NAT firewall routers) keeps logs but they do not contain ANY valuable information. Here is a piece of the log taken during a port scan:
Like I said, you may be under attack and even if you inspect your router logs you won’t know it’s happening. OS X’s firewall will not offer much additional information, the screenshot earlier mentioning iStatServerDeamo is the only entry that appeared in the log during this port scan. As the traffic did not get past the router there is nothing for the OS X firewall to log.
While the AirPort Extreme does a poor job of hiding your presence and logging suspicious (or any useful) activity this does not mean your NAT router does the same. I’ve owned several routers in the past that used NAT as a firewall but offered a few more options like enabling stealth, blocking DoS attacks etc. (Linksys, Draytek) but their logging capabilities were all pretty bad.
SPI (Detection good, Prevention good) – Stands for Stateful Packet Inspection and is, unlike NAT, designed to inspect and filter unwanted traffic (data packets). It is able to stop and inspect a greater number of packet contents before determining if it’s allowed through and inspects outgoing traffic as well. This greater level of scrutiny is considered to provide much more robust security and better information on network traffic. SPI is also capable of pattern recognition like a port scan or continuous probing on a single port and can adjust it’s response accordingly. SPI typically offers a great detail of logging as well. If you plan to open up any ports and use port forwarding so you can access certain applications and services from another location or just want more/better security in general you should definitely consider an SPI firewall.
I recently acquired one that uses a range of protection and detection techniques like SPI, NAT and IDP and for comparison here is that same port scan again. This time there is just the SPI firewall between the modem and Mac Pro.
And here are the scan results:
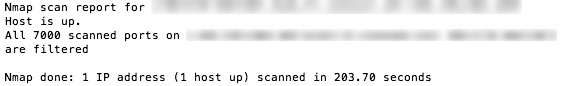
As hoped and expected, I am completely shielded from the outside world. The firewall detected a port scan was being performed, did not give a single response to the scanner and blocked any probes from entering my network. When checking the logs entries like this show up:
![]()
![]()
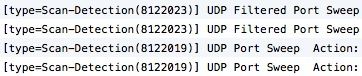
Much better and detailed logging. This is what I look for and expect from a firewall. I still have OS X’s built-in firewall enabled and Little Snitch installed as additional layers of security though. (I can’t think of a scenario in which Little Snitch is not recommended)
DPI (Detection best, Prevention good) – Stands for Deep Packet Inspection and is SPI’s big brother. Able to stop and inspect every packet passing through it thoroughly (like reading the contents of an email) before allowing or rejecting it. This level of filtering is typically found in higher end security gateways.
NAT + SPI/DPI – As this implies it is a combination of techniques. Routers and firewalls that offer SPI/IDP also have a NAT feature to help with routing and add a layer of security to an already secure device.
Other features found in good (and possibly more costly) firewalls are IDP (Intrusion Detection and Prevention), Application and content filters and more. As the list of good features grows the price usually goes up. I hear a lot of knowledgeable people (when it comes to stuff like this) say that SPI in consumer grade routers is about as effective as NAT but noone has been able to provide me with any documentation or studies to back this up. I think this may be old and outdated information that some folks just don’t want to let go (like those still persisting there are no viruses for the mac etc.) By design SPI is better than NAT so I have a hard time believing this claim but security works best in layers. Don’t think you are off the hook if you have a good firewall in place, add layers of security by enabling OS X’s firewall, install Little Snitch and run an antivirus application. Keep router and firewall firmware up to date at all times and inspect the logs for unusual activity. As I mentioned before detection is as important (if not more important) as prevention so I put a lot of value in a router/firewall’s ability to keep good logs.
OS X’s built-in firewall works in two ways; a basic packet-filter checking each packet for type, port number, origin and destination and it also uses an application (or socket filter) firewall combining the packet filter method and a list of pre-approved applications to determine if traffic is allowed to be received. Still, if your Mac connects directly to a cable or DSL modem that has no additional features like built-in wifi and has only one ethernet port, it almost certainly has no firewall or protection of any kind. If this is the case for you I would recommend investing in a hardware router/firewall and at the very least have OS X’s built-in firewall enabled.
Am I a target?
If you have any personal or financial information on your computer and that computer is connected to the internet, then yes. Personal information (like your own and everyone in your email/address book) can be sold to spammers and scammers, financial information can be used by the thief or sold as well to the highest bidder. Even if your computer is blank with just the OS, it has value to someone with malicious intent that is scanning the net for machines to exploit and join a botnet. This sound very ominous I know but even if someone is not specifically out to get you, there are many automated bots scanning IP ranges all across the internet looking for open ports and vulnerable devices to exploit, any device on your network can become a target.
How do i know if my firewall is doing it’s job?
There are a few online free services that will tell you the basics but a real test has to be done by a skilled pentester (Penetration Tester) that can test your firewall and other components of your network. Of course good pentesters are not always easy to find and usually cost quite a few bucks once you do find them, so for now here are some ways to test your firewall:
ShieldsUp – This is an online service that can perform a few scans of your IP address and you can find it here. After clicking the ‘proceed’ button you are presented with a few different options. A good start would be the ‘All Service Ports’ option as it gives you a nice overview of the first 1056 ports scanned. Green means the port is hidden, blue means the port is closed and red means a port is open (take care of that!). While closed ports are good, if you prefer to be hidden then you’ll be looking for a result like this:
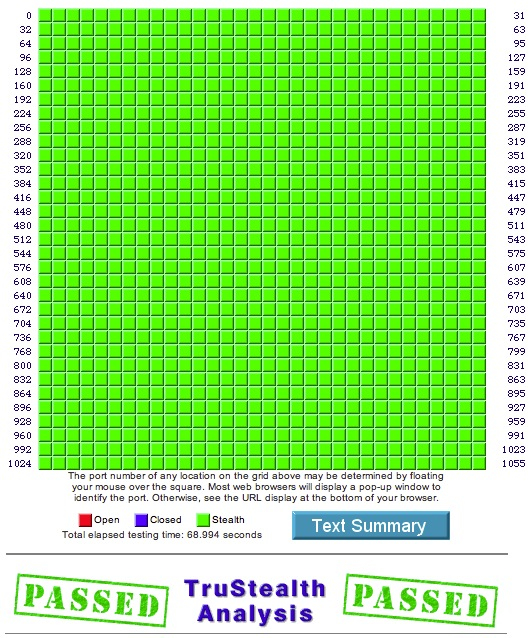
Nmap – A free piece of software that runs on all platforms and is controlled through the command line (Terminal) on OS X. The installer offers a GUI version as well (Zenmap) but I find the command line easier. The port scans I mentioned in this article were done with Nmap because it offers different scan types and levels of aggression. Nmap can reveal more than OS X’s own Network Utility can for example.
Nmap has to be used on a clean machine for best results. If you have an antivirus running or use sharing services on your Mac or router you can get plagued by false positives. For example running Nmap from a Mac that has Avast antivirus installed will tell you that the target you just port scanned has ports 80, 110, 143, 993 and 995 open. These ports may not be open at all but because Avast runs on your Mac and monitors those ports it can confuse Nmap and give you false results. False positives can send you running in circles looking for open ports that aren’t there so be careful with this, if you can then verify your scan from another location as well.
Speaking of location, you want to run Nmap from a location outside of your network for best results. I used a Mac I control via Remote Desktop in another country and a friend in yet another country helped me verify all the scan results as well. Running Nmap to scan a network you are currently in can give a lot of false positives and list ports that may not be open to the outside world (internet) at all. A good tool to have as it can be used to test your own network in a variety of ways, not just with port scans.
You can read more about Nmap here and download it here. A few quick samples you can use to get started (use these without the quotes, replace 00:000:00:000 with the IP address you want to test):
“nmap 00.000.00.000” – The most basic port scan, scans 1000 most commonly used ports.
“nmap 00.000.00.000 -p 1-7000” – The -p tells Nmap you want to scan a range of ports, I used range 1 to 7000 but you can go as high as 65535 if you want.
“nmap 00.000.00.000 -Pn” – The -Pn forces a scan of the target IP even if it is hidden or maybe not even online.
These basic commands will get you started. Type “nmap” (without the quotes) without adding an IP to reveal the manual.
Logs – An important part of security is detection. See if your router/firewall has logging capabilities and inspect the logs. See if the port scans you performed showed up in the logs and if it gives you enough information to act on if needed. Just as frequently inspecting the logs is important, so is testing your network. Use the ShieldsUp service or Nmap once in a while to see if your network is still secured. Just like fire drills, after all you do not want to find out something is wrong at the time of a fire.
Now before you run out and buy a brand new router or firewall there are a few things to keep in mind.
1. While NAT is not the best defense it is good enough for the majority of consumers. If you want more detail in your logs, more control over the firewall or just want piece of mind then look for a firewall that offers SPI or a mix of techniques I covered earlier.
2. If you already have a router or other kind of gateway, log in to it, update the firmware (if possible. Routers and modems you rent from your provider are usually locked. This means outdated firmware with possible old unpatched vulnerabilities) and check all settings. If a firewall is present look for features I mentioned, if you do not find such features, see #1.
3. If you do decide you want the added protection of a stateful inspection firewall and detailed logging so you can monitor the network activity, there is no need to throw out your existing router. Instead just add a firewall between your modem and router and set your router in bridge mode so it leaves all the heavy lifting to the firewall box. If your current router has Wi-Fi capabilities there is no need to buy a firewall that also has Wi-Fi capabilities. Get an ethernet only firewall box and use the router in bridge mode to handle your Wi-Fi for example. By adding to the network rather than replacing existing gear you also have a backup in case one of the devices fails.
If you feel like your Mac is well enough protected and you do not need additional protection, stop and think for a moment to see if this applies to your entire network. Other computers, smartphones, tablets, IP cameras, network printers etc. If you are not confident that every device on your network is secure it may be worth investing in a more capable hardware firewall or router.
You want the best detection and best prevention and I do not believe a single product or service offers that. Sure a state of the art high end unified security gateway with all the bells and whistles (NAT, SPI, DPI, IDP etc. etc.) will most likely do a great job but it will also cost you a few grand and the learning curve is huge. Even with a box like that there needs to be security on the computers in the network (OS X built-in firewall and Little Snitch for example), logs have to be inspected, firmware needs updating and the occasional testing has to be done. Security changes all the time and you have to evolve with it to make sure you don’t end up a victim. Last year an 8-character password was considered good security, now it has to be way longer to be secure. A few years ago Mac users laughed at the thought of antivirus, now most (but not nearly enough unfortunately) know it’s a good idea to have. Just like these two examples there are plenty more to show how quick the security field can change. Do you need a firewall? Absolutely. Is a firewall alone enough? No, the best security comes in layers and there must be a way to detect possible malicious activity.
A big thank you to Johnny and Cobie for helping me with the scans!
Any comments and feedback are welcome.
Wow that’s a lot of info. I enabled the firewall in my Mac some time ago but never ever did it occur to me to check the logs. Same goes for my AirPort Extreme. You are right, the AP logs are useless and the OS logs are limited. The Shieldsup scan showed a mix of closed and stealth ports with 4 ports open that i was not aware of. I am definitely interested in getting a firewall to add to my network after reading this (and testing for myself). I don’t think anyone pays any mind to the detection part of things, great article!
You mention you recently got one, which one did you buy?
I checked and compared a lot of brands and was stuck on Draytek and ZyXEL for a while. In the end I went with a ZyXEL ZyWALL USG20, their most basic option. I purchased based on detection and logging capabilities but it turns out the prevention is pretty damn good as well 🙂 Price was good too (got it through Amazon). Slight learning curve as it’s not like setting up your average home router but a lot of good resources out there willing to help.
I had a friend who is familiar with some pentesting techniques take a stab at my configurations. I ran the same setup as you with my Mac connected directly to the modem and then with the airport router. The firewall log in Mac OS is indeed limited and the airport extreme log is garbage. Will run some more tests and let you know if something interesting pops up.
Oh nice! Definitely be interested to hear the results of his tests 🙂
Good article. I checked the logs of my linksys and apart from renewing DHCP leases and basic stuff like that there is no mention of the portscan I did with shieldsup. I think the Mac OS firewall and AirPort Extreme (and Time Capsule) firewall are enjoying “security through obscurity”. I’ve searched and can’t find a single test or study that really put either one of those firewalls through their passes by really attacking it and trying to hack it. They might be great, they might prove not to be once a skilled tester really gets to work on them. I hope someone will one of these days as these products are depended on by more and more people. Agreed with the poster and earlier comments, the logs need a lot of work. Perhaps it will be better in the next update.
The OS X (more specifically the ipfw unix firewall) does have a good reputation. If there were major flaws and vulnerabilities in it we would definitely be able to find news about it online I think. The AirPort Extreme does worry me a bit, NAT does a decent job of keeping unwanted stuff out but as it is a ‘dumb’ firewall I’m very interested to see what results of actual pentests or attacks would be (hopefully we’ll hear back from Ann67 on that 🙂 ). You bring up a good point, the next version of AirPort firmware or OSX may bring better logging. For the AirPort and Time Capsule I really doubt logging improvements will be made or more ‘intelligent’ features will be added but 10.9 Mavericks may carry some changes, will run a few tests on that and post results.
(of course keep in mind 10.9 is still in beta stage) I ran a scan of the first 7000 ports and found the following:
6999 ports filtered, 1 port open (port 548, file sharing). The firewall allowed a TCP connect to the file sharing port and the log shows this. When i make a valid connection with my user account though the log entry is the same, it makes no distinction between a probe, unauthorized/denied connection request or a valid connection request. Also the actual port scan resulted in log entries that are not at all helpful. “Stealth mode connection attempt to TCP 2159 times” is all that is mentioned, no source IP, no mention of specific ports being scanned etc.
Of course 10.9 is still in beta but this is definitely something to keep an eye on when the final release becomes available. Right now the firewall logs in 10.9 are useless.
On the flip-side, if you want to profile your outbound firewall rules, you can use IsMyPortBlocked (www.ismyportblocked.com).
It can send actual data from it’s java client on your machine inside your firewall to the IsMyPortBlocked server in the cloud over any TCP or UDP port, thereby profiling any and all firewall rules that would affect the IP address from which it’s run.
The Privacy Policy and Terms of Service make me not trust that service too much. Also, no SSL is used and nowhere does it state my privacy and security are being protected by IMPB, it even states it may be violated! “The Website may also contain material that violates the privacy or publicity rights”. Then there is the use of Java which is not recommended. I do not recommend that website to my readers.
i use a tomato router connected via ethernet to my Fios actiontec router, would a firewall in-between be advantageous?
Very helpful and informative. Thanks!