SSL Vulnerability fixed in iOS but not in OS X
Yesterday Apple released iOS 7.0.6 and 6.1.6 to fix an SSL connection verification issue. While Apple’s description about the fix is nice and vague as always, this bug was extremely important and has since been found in OS X 10.9.0 and 10.9.1 Mavericks as well.
Before you panic and never use your Mac again it is important to know that this flaw can only be exploited (as far as I know) when someone is on your network. Before you say “Oh then I’m safe” or “Noone wants to hack me” please do not underestimate this vulnerability. It’s not just Safari but also Mail, Messages and possibly iCloud, iTunes and other OS X components as well that are affected. Until Apple releases a fix it is more important than ever to stay far away from public wifi (Starbucks, Apple Store etc.). You may also want to stop using Safari and switch to Firefox as it is not affected by this flaw. Use webmail (through Firefox) instead of Apple Mail and to make sure all your internet traffic is secured using a VPN might not be a bad idea either.
One of the websites where users can test to see if their browser is vulnerable to this flaw is gotofail.com where a quick browser test will reveal the following for Mavericks users:

However I have noticed that the first time I opened this site, Little Snitch alerted me to unusual activity:
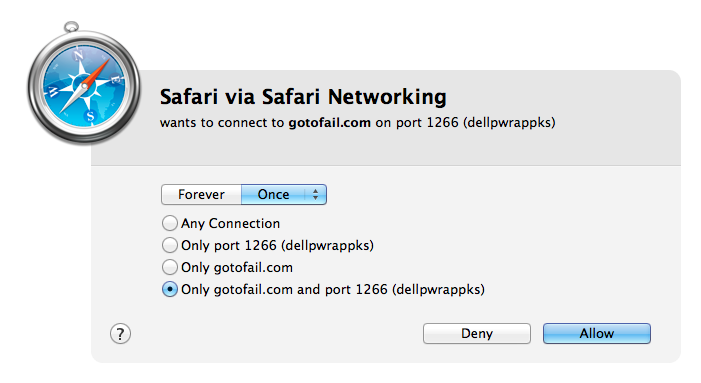
A website attempting to connect on a port number other than 80 (http) or 443 (https) is not normal so Little Snitch asked for my permission first. When I select “Deny” the website will show me the following:

I do not know if Little Snitch would jump in like this in every scenario the SSL flaw can be exploited but it helped me in this case. This vulnerability can use the 443 port though, in this case Little Snitch may or may not be aware of something dubious going on, I have not been able to test this as the test sites use a different port number (Thank you Arnaud for pointing this out). A 3rd party patch is available but I have chosen not to install this myself as I don’t know the developer. If you want to read more about it go here. Another test site can be found here.
This vulnerability has been there for several months and may have been exploited in the wild as a 0-day, now the whole world knows about this so it may be exploited far more until Apple releases a fix. From the reports it appears that the current OS X 10.9.2 betas that Apple developers are testing are still vulnerable indicating Apple may not have been aware of the flaw in OS X. Hopefully 10.9.2 will be updated and released very soon or at least push out a supplemental update to fix just this one flaw. Until then:
• Use Firefox, not Safari. Or use your updated iOS device for web browsing.
• You can also use Chrome as it is also not affected but I will always recommend Firefox over Chrome.
• Use webmail in Firefox, not Apple Mail. Or use your updated iOS device to send and receive mail.
• Consider installing Little Snitch, a great tool in general.
• Stay away from public wifi, open wifi or wifi with weak passwords. Make sure your own network is secure.
• Make sure your iOS device has version 7.0.6 installed. Go to Settings > General > Software Update. iOS 6 also appears to be affected so iOS 6 users should install 6.1.6.
For more details on this vulnerability you can check out these websites:
Sophos NakedSecurity (very well explained)
ImperialViolet
Ars Technica
Graham Cluley
They all cover the technical details as well.
[UPDATE] Researcher Ashkan Soltani posted a list of applications that use the same framework that is currently vulnerable. Calendar, FaceTime, Keynote, Mail, Twitter, iBooks, ApplePushService and Software Update.
Apple has stated a fix for this issue is coming “very soon”. This was late Friday and at the time of this update it’s Monday morning. No fix has been released as of yet, maybe it was not important enough to have people work on this over the weekend?
I’ll add to this article as more details become available.
2 thoughts on “SSL Vulnerability fixed in iOS but not in OS X”