XARA sets it’s sights on OS X and iOS
Researchers have discovered “a series of high-impact security weaknesses, which enable a sandboxed malicious app, approved by the Apple Stores, to gain unauthorized access to other apps’ sensitive data.” Sounds ominous huh? It is.
The researchers built a malicious app, submitted it to Apple, beat all the tests and security screenings and got the app into the App Store. This app was able to snatch data from the keychain (where all your passwords live on a Mac) using a very simple trick. Your keychain allows the sharing of resources. Your stored facebook password for example can be accessed by other applications if you allow it. This app created a false entry for facebook stored login credentials. Next time the user actually logs in to facebook the login details are stored in the keychain entry created by the malicious app. Now the app has your facebook login credentials. You can imagine a truly malicious app by malware creators will go after your entire keychain and harvest whatever it can. They routed their app through Apple to make a point but of course malware can come from any source.
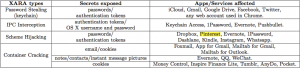
The above described method is just one of the cross-app resource access (XARA) attacks that were performed. WebSocket and Scheme were also tested and did not fare well. Even the implementation of sandboxing (making sure each app stays in it’s own confined space and can’t access data it shouldn’t) Apple uses was found to be flawed “exposing an app’s private directory to the sandboxed malware that hijacks its Apple Bundle ID.” The Bundle ID is is a unique identifier for each app that comes from the App Store. Applications that use bundled helper apps like 1Password have a Bundle ID but the helper app does not. In the case of 1Password that would be the browser extension. The researchers found that they were able to intercept traffic between 1Password and the browser extension, giving them access to the things you don’t want anyone to access.
1Password has been working on this issue for a while and has yet to find a fix. All they can do is recommend users always keep their 1Password Mini running and pay attention to what you install. The reason for their first suggestion is that the researchers launched the malware before 1Password Mini and were able to accomplish the intercept of sensitive data. If 1Password Mini launches right when you log in to your Mac, the malware should not be able to get between 1Password Mini and the browser extension. Agilebits full discussion on this topic can be found here.
To allow applications to communicate with their helpers they often set up a server. In the case of 1Password, the application runs a server and opens a few different ports waiting for requests from the browser extension. That inter-app communication is the weak link. It might even be the communication between the 1Password Mini and the 1Password app, I’m not sure. Either way, there is no fix as of yet. Disabling the browser extension won’t help, disabling 1Password Mini won’t help and clearing all names and passwords from your system and keeping them in a notepad is not only a very bad idea, it’s just impractical.
“Fundamentally, these problems are caused by the lack of app-to-app and app-to-OS authentications.” the reearchers pointed out. To see just how widespread these issues were, they developed a scanner that automatically analyzed OS X and iOS app binaries.
“In our study, we ran the analyzer on 1,612 most popular MAC apps and 200 iOS apps, and found that more than 88.6% of the apps using those mechanisms and channels are completely exposed to the XARA attacks, and every app’s container directory has been fully disclosed. The consequences are dire: for example, on the latest Mac OS X 10.10.3, our sandboxed app successfully retrieved from the system’s keychain the passwords and se- cret tokens of iCloud, email and all kinds of social networks stored there by the system app Internet Accounts, and bank and Gmail passwords from Google Chrome; from various IPC channels, we intercepted user passwords maintained by the popular 1Password app (ranked 3rd by the MAC App Store) and the secret token of Evernote (ranked 3rd in the free “Productivity” apps); also, through exploiting the BID vulnerability, our app collected all the private notes under Evernote and all the photos under WeChat. We reported our findings to Apple and other software vendors, who all acknowledged their importance.”
Affected apps and services include iCloud, Gmail, Google Drive, Facebook, Twitter, Chrome, 1Password, Evernote, Pushbullet, Dropbox, Instagram, WhatsApp, Pinterest, Dashlane, AnyDo, Pocket and several others.
I can go on and on sharing every step of the research, rag on Apple for not fixing these issues (they have known since October 2014) and get into the technicalities but for now all you need to know is this:
• These vulnerabilities are huge and there is no fix.
• Now that the news is out, bad guys will jump on this and implement it in their malware.
• Right now no known malware uses these techniques.
• Malicious apps can come from any source, including the App Store.
Until more is known and Apple provides a fix, continue using your best practices.
• Don’t install software unless you absolutely need it.
• Whatever you do install should come from a well known reputable developer and only from original sources (developer website or App Store).
• Use Little Snitch. Any malicious application that uses these techniques will have to send your stolen data somewhere. Little Snitch will show you that outgoing connection attempt and if it’s something you don’t recognize or find suspicious, block it. In theory, even if you were to be infected with this type of malware, the stolen data will remain on your system.
Unfortunately iOS does not have a Little Snitch and was found to be vulnerable as well, though not as much as OS X. So be extra careful with what you install on your iDevice.
[UPDATE] Friday June 19th.
Apple has commented stating: “Earlier this week we implemented a server-side app security update that secures app data and blocks apps with sandbox configuration issues from the Mac App Store,” an Apple spokesperson told iMore. “We have additional fixes in progress and are working with the researchers to investigate the claims in their paper.”
The full report can be found here. (PDF, Links to Google Drive)
A youtube video that shows how one of the exploits can work can be seen here.
A youtube video that shows how a WebSocket attack against 1Password is done can be seen here.
And how to steal iCloud tokens in a Keychain attack… here.
Thanks, excellent! Will go for Little Snitch!