Security flaw found in Safari
Security researchers have flagged a simple but potentially dangerous flaw in the Apple Safari browser, which could be used to hijack users’ web sessions. The problem lies in the Apple Safari webarchive format, which saves all resources on a web page into one document. To exploit the flaw, an attacker would have to trick a victim into opening a malicious webarchive file, either by forced download or via an email attachment in a spear phishing attack. “Safari’s webarchive format saves all the resources in a web page – images, scripts, stylesheets – into a single file. A flaw exists in the security model behind webarchives that allows us to execute script in the context of any domain (a Universal Cross-site Scripting bug). In order to exploit this vulnerability, an attacker must somehow deliver the webarchive file to the victim and have the victim manually open it (e.g. through email or a forced download), after ignoring a potential “this content was downloaded from a webpage” warning message.”
This flaw was reported to Apple in February 2013 by Rapid7, who discovered the flaw, but Apple has done nothing to patch this vulnerability. “Unfortunately, Apple has labeled this a “wontfix” since the webarchives must be downloaded and manually opened by the client. This is a potentially dangerous decision, since a user expects better security around the confidential details stored in the browser, and since the webarchive format is otherwise quite useful. Also, not fixing this leaves only the browser’s file:// URL redirect protection, which has been bypassed many times in the past.” writes Rapid7.
A lot of sensitive information is stored in your browser’s cookies so this information has to be protected. Since Apple appears to have no desire to fix this we are suggesting a small work-around that can protect you from accidentally opening .webarchive files in Safari on your Mac. Our work-around basically forces the Mac to open .webarchive files in another application that does not have access to your cookies. We recommend users do this on every Mac they own and system administrators to do this for every Mac in the office.
1. Create a webarchive to work with.
In Safari right now, go to the ‘File’ menu and click ‘Save As’. A window will pop up allowing you to save the website as a webarchive. Make sure the format is set as ‘Web Archive’. Then save it on your desktop.
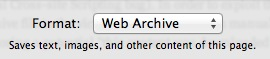
2. Creating the work-around.
Right-click on the webarchive file you just saved and select ‘Get Info’.
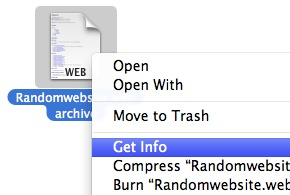
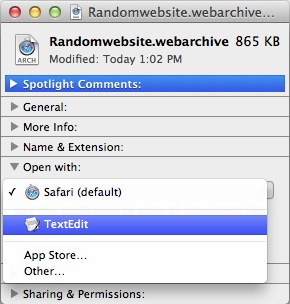
Once the Information window opens, find the ‘Open With’ section. This should currently read ‘Safari’. Click on the menu that says ‘Safari’ and change this to ‘TextEdit’.
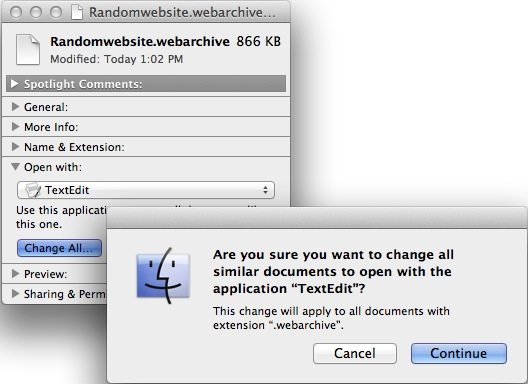
Now click the ‘Change All’ button and confirm by clicking ‘Continue’.
Even if you open a .webarchive file from now on, wether you were tricked or just not paying attention, it will open in TextEdit. Test it by opening the webarchive you just created, once confirmed it works and TextEdit does indeed open the archive, you can delete the webarchive file. TextEdit will still show some of the contents and allows you to click on links and such but it does not have access to the sensitive information stored in your cookies. If you have webarchives that were already saved or you know they are safe/from a trusted source, just drag the .webarchive file onto the Safari icon in your Dock or right-click > Open with > Safari. This will leave the default application set as TextEdit but will open that particular webarchive in Safari.
A work-around for now that should keep you safe from this exploit.
Be careful and spread the word.
Sources:
TechWeekEurope
Rapid7
Thanks again! 🙂